Use Cases
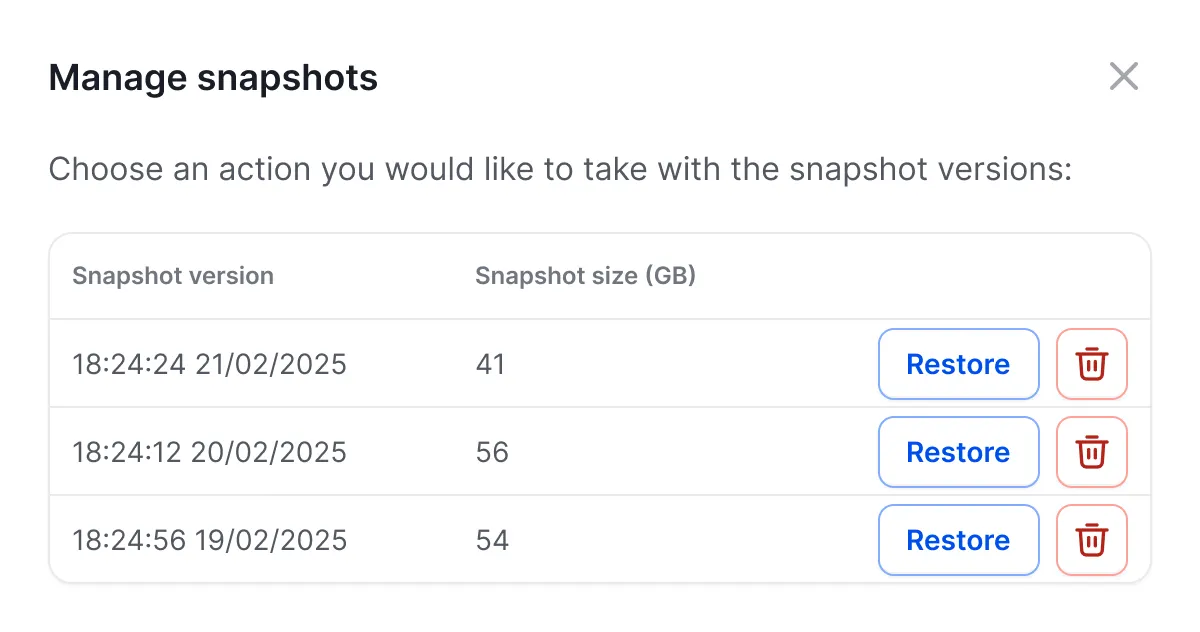
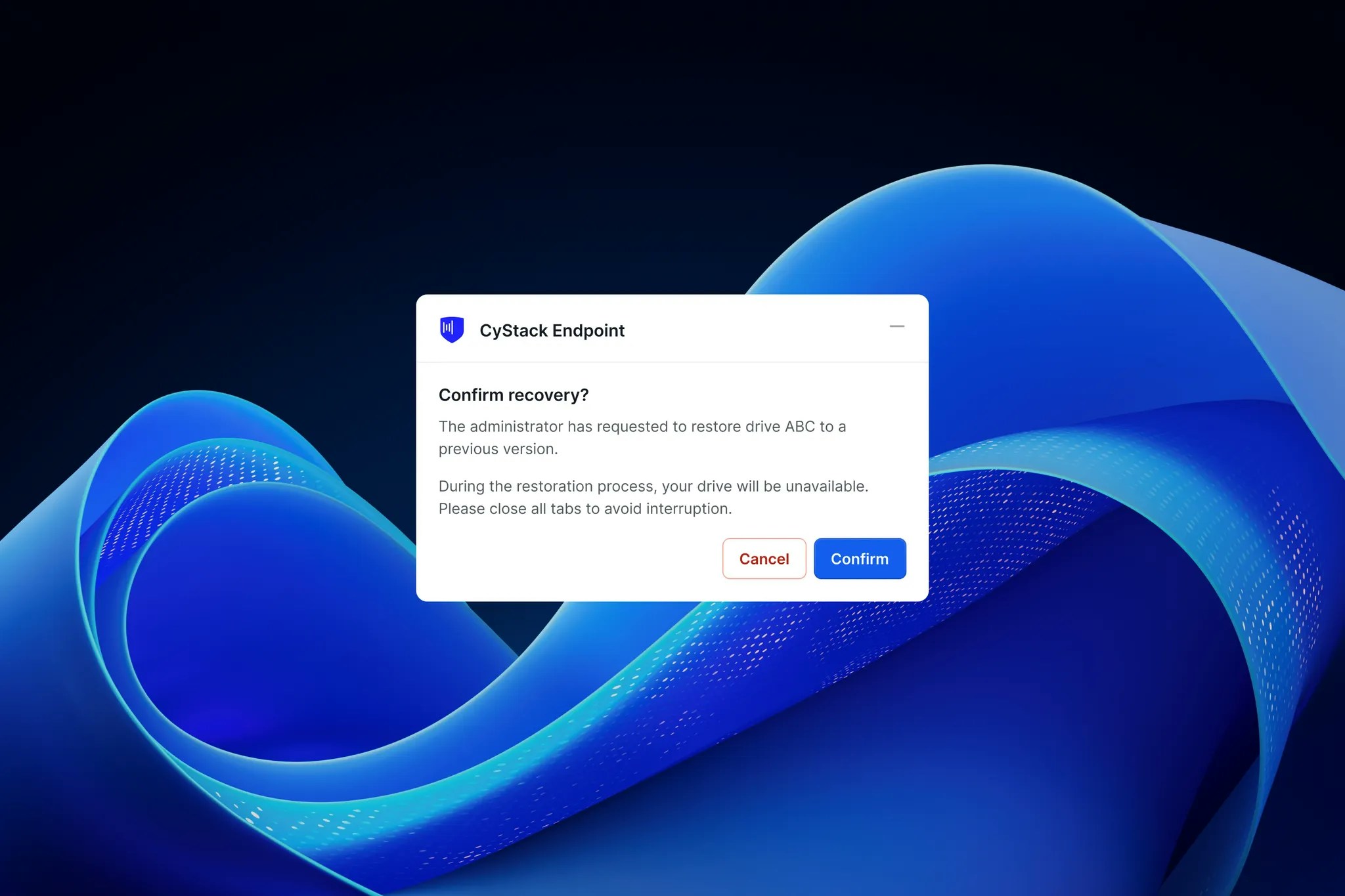
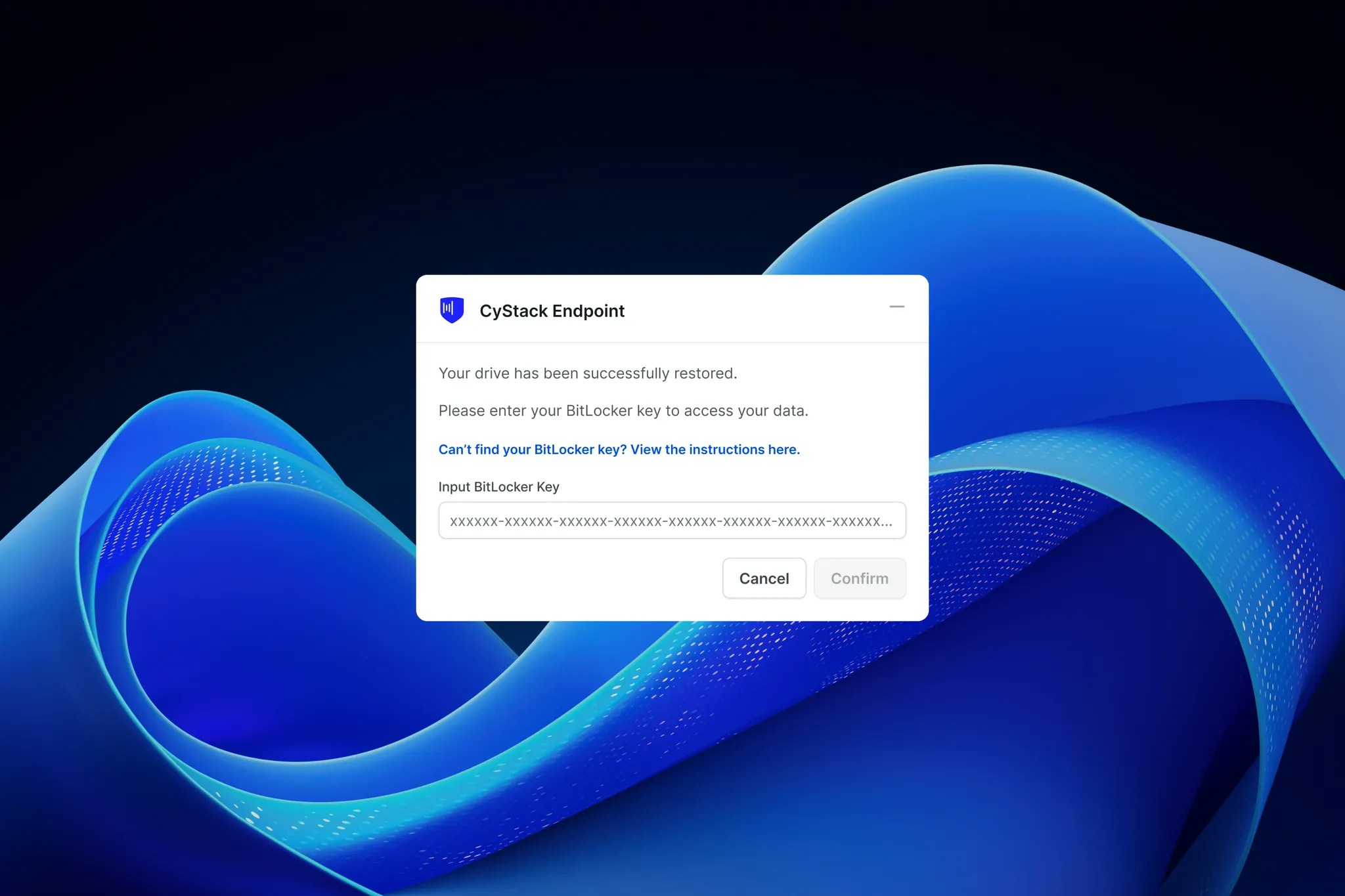
- In the event of a hard drive failure or device theft, you can retrieve the latest data snapshot to minimize downtime and get employees back online quickly.
- If data is encrypted by ransomware or files are maliciously deleted, clean data can be restored from previous backups, mitigating business impact.
- When provisioning new devices or during employee transitions, critical data can be seamlessly transferred to the new hardware.
Backup via AWS S3 Storage
AWS Configuration for CyStack Endpoint
-
Prerequisites: Ensure you have an account with appropriate permissions for IAM and S3 services. Generate a security key and run the following command to configure AWS CLI credentials, enabling the CLI to interact with AWS services:
-
Replace the placeholders
[USER_NAME],[REGION],[ACCOUNT_ID],[BUCKET_NAME],[ROLE_NAME], and[POLICY_NAME]with your actual values.
1. User
2. Bucket
3. Create Necessary Roles
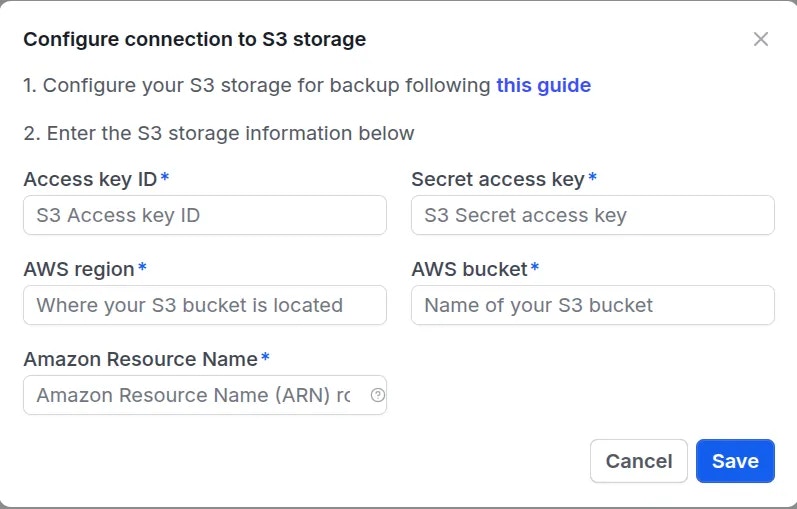
4. Configure Connection from CyStack Endpoint to Storage Repository
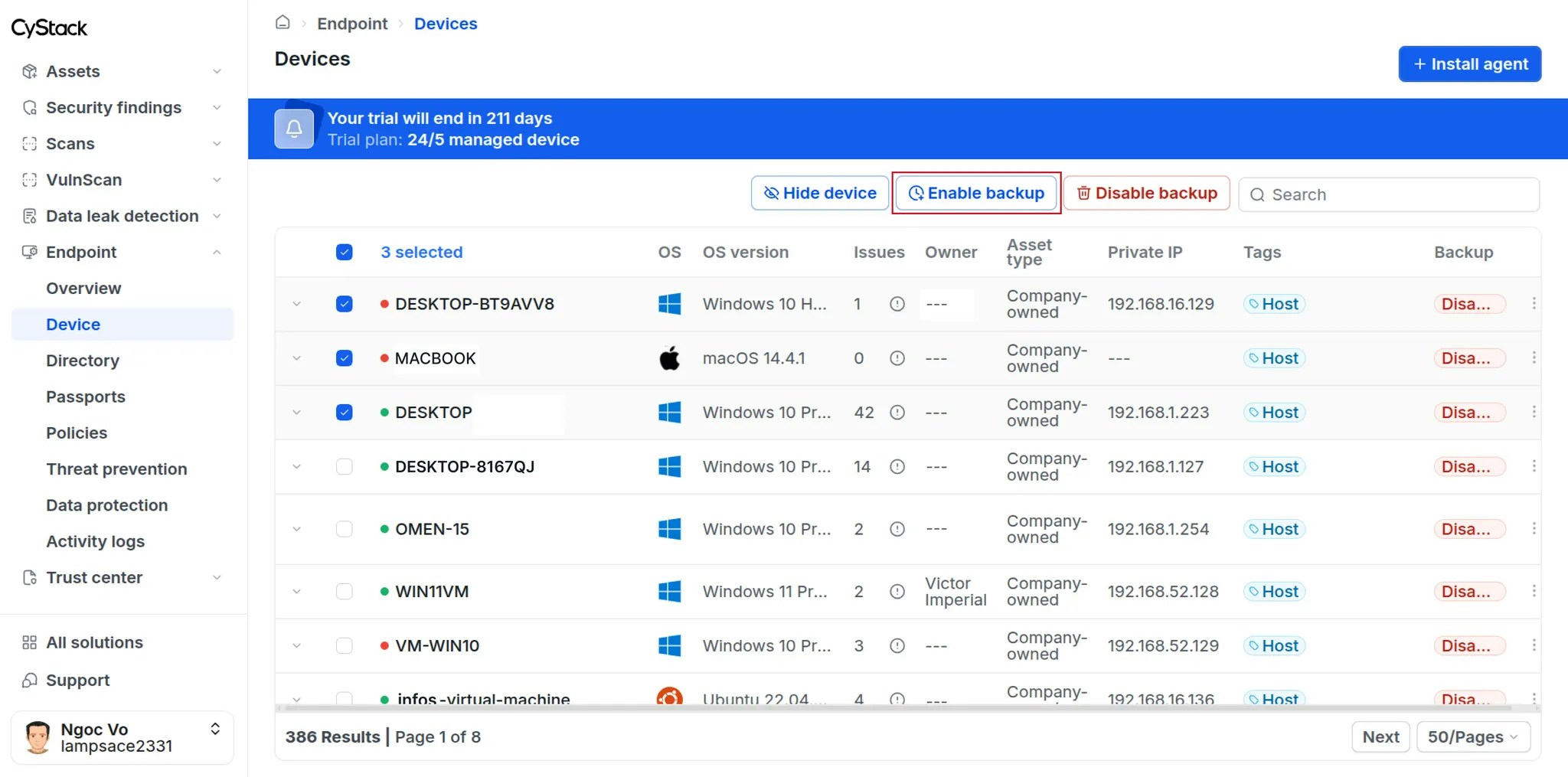
Data within the enterprise drives on selected devices will be automatically backed up every 6 hours. The backup process supports the following file types:.doc, .docx, .odt, .ott, .pages, .xls, .xlsx, .csv, .ods, .numbers, .pdf, .ppt, .pptx, .odp, .key