Was this helpful?
Filters and search
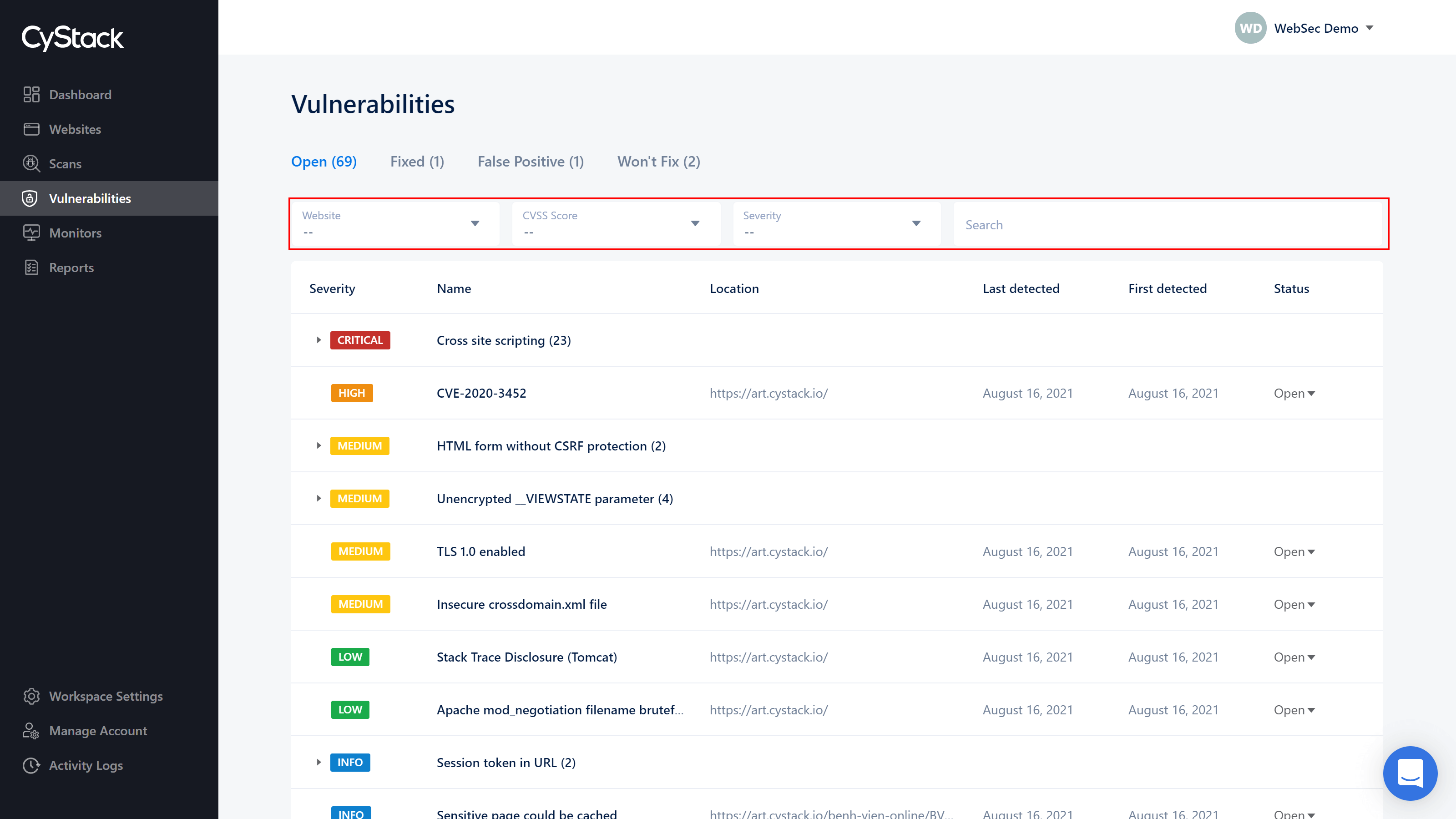
Customers can search for a specific vulnerability by entering the keyword in to the Search box, or filter the vulnerabilities in their corresponding Status tab for better management:
- By Websites
- By CVSS Score (Common Vulnerability Scoring System - an open framework for communicating the characteristics and severity of software vulnerabilities).
- By level of danger: critical, high, medium, low and info
Severity
CyStack Web Security provides a system of rating vulnerabilities based on their CVE, CWE and other criteria, with 5 levels:
| Severity | Impacts | Example types |
|---|---|---|
| Critical | - Exploiting the vulnerability could take control of the server or other infrastructure device on which the application operates. - Vulnerability allows escalation of privileges, from anonymous or normal user to administrator. - Vulnerability allows stealing sensitive data such as financial, personal information of users, types of passwords, tokens, API keys. - The attack is completely direct, there is no need to use phishing and social engineering forms to collect information from people. | Remote Code Execution, Authentication Bypass, XML External Entities Injection, SQL Injection, Database leaking |
| High | - Exploiting the vulnerability can lead to privilege escalation, from anonymous user to normal user. - Vulnerability can lead to data loss or disrupt access. - Vulnerabilities that change the features designed in the product. | Stored XSS, CSRF at sensitive pages, IDOR, SSRF |
| Medium | - Usually, attackers must use phishing and social engineering techniques to collect information from victims to reach the system. - Exploitation requires the attacker to operate on an intranet zone with the target. - Mining yields only a very limited amount of information. - Vulnerabilities require higher user permissions for successful exploitation. | Reflective XSS, URL redirect, CSRF at less sensitive pages |
| Low | - The attack has a very low impact on the target's operations and data. - Exploiting often requires physical or local access | SSL misconfigurations, SPF misconfiguration, Self-XSS |
| Information | - The vulnerabilities are not functionally exploitable. - The vulnerability is by design or the risk it poses is considered acceptable. | Debug information, Using CAPTCHAs, Code obfuscation, Rate limiting. |
CVSS score
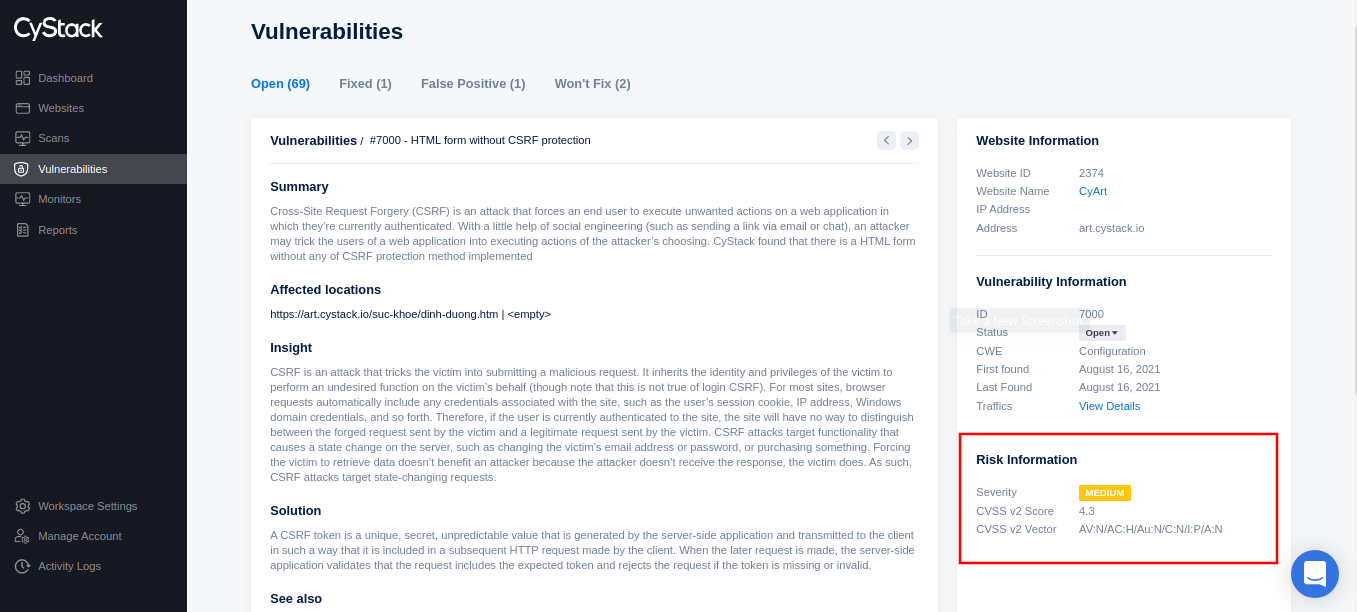
CyStack Web Security also provides information about vulnerabilities following CVSS v2, including CVSS v2 Score and CVSS v2 Vector, shown in Vulnerability Details.
Need more help?
